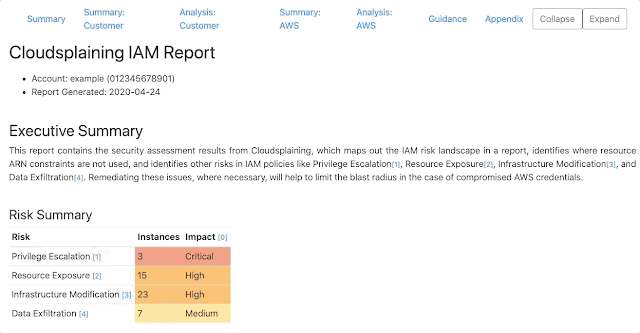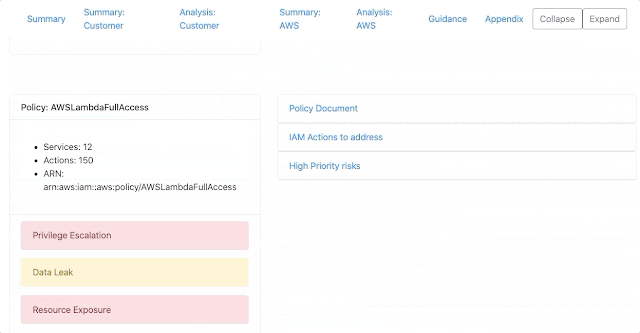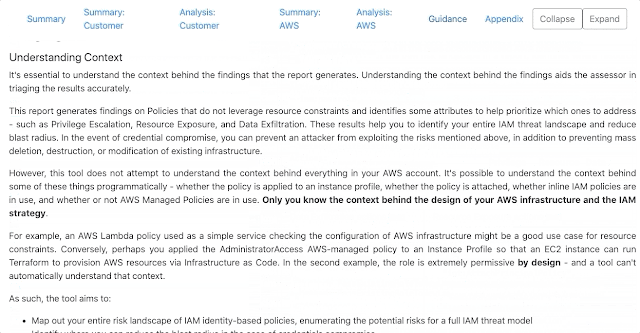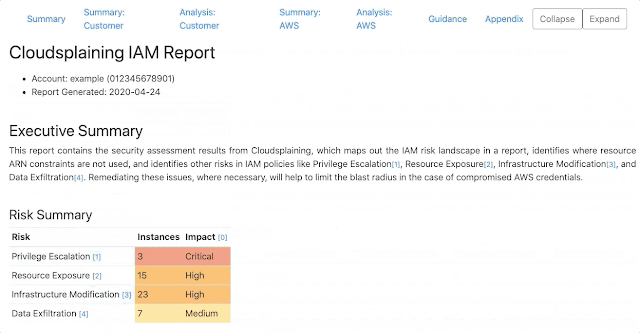
Cloudsplaining - An AWS IAM Security Assessment Tool That Identifies Violations Of Least Privilege And Generates A Risk-Prioritized Report

3 Best Tools and Security Protocols for a Successful IAM | by Successive Digital | Successive Digital | Medium