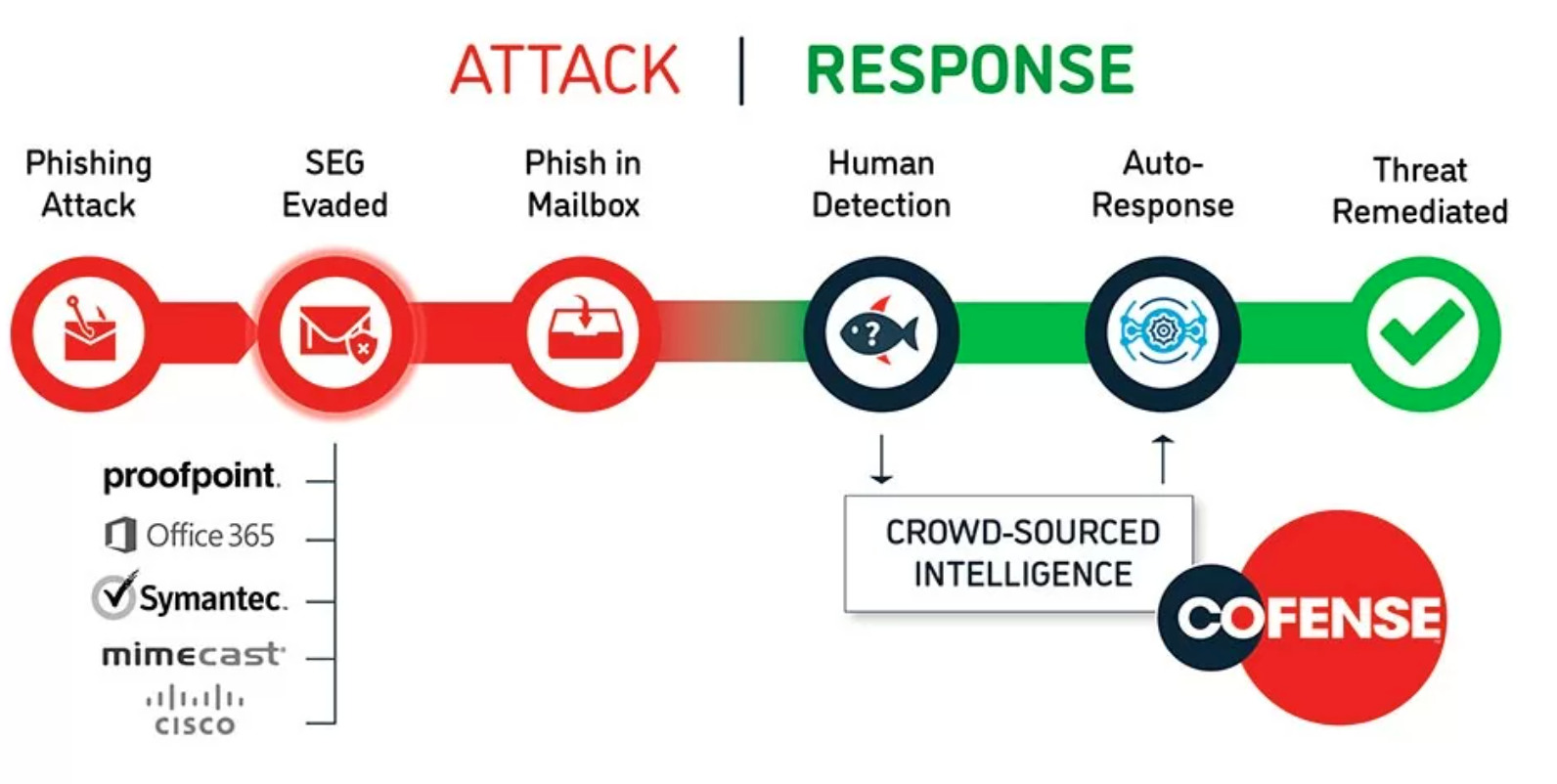
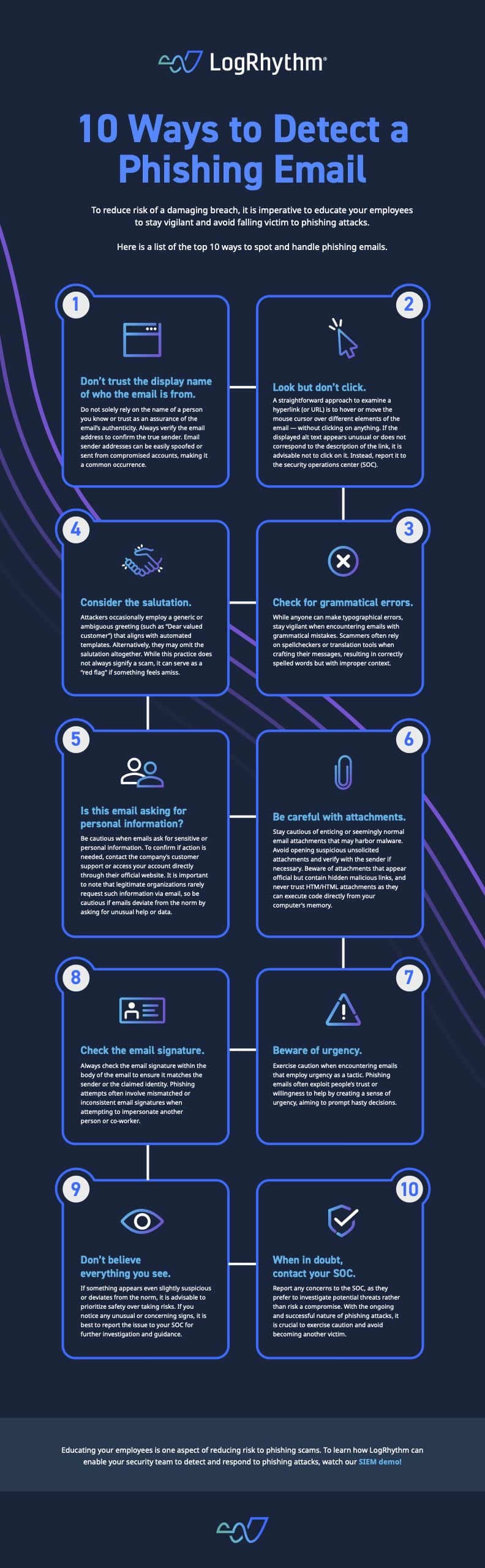
How Organizations Can Use Advanced Threat Protection Solutions for Email Security, Such as Anti-phishing, Anti-spoofing, and Anti-malware Tools - PhishProtection.com
Ptrace Security GmbH on X: "This is Advance Phishing Tool ! OTP PHISHING https://t.co/OeXFjIesXT #Pentesting #Phishing #CyberSecurity #Infosec https://t.co/gnigIbcVoO" / X






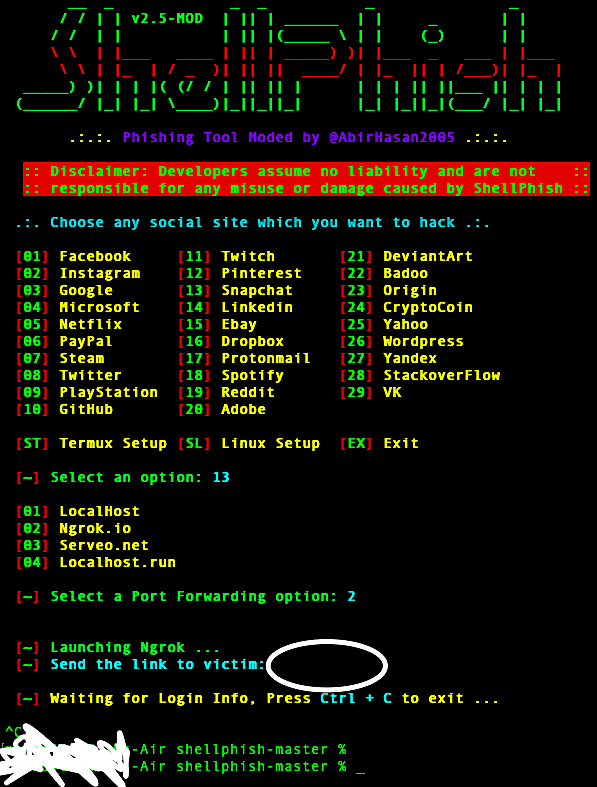


![Top 8 Different Phishing Tools with Features [2023] Top 8 Different Phishing Tools with Features [2023]](https://cdn.educba.com/academy/wp-content/uploads/2021/07/Phishing-Tools.jpg)